Key factors to consider when planning a cybersecurity budget
Every business has a basic group of factors to consider when determining its cybersecurity budget:
- Company size and location
- Industry/sector
- Compliance requirements
- Type of data collected/stored
- Sensitivity of their data
- Mandates from the board of directors
- Local, state and federal regulations
Critical business functions
What are your business’s top priorities? Determining these functions based on the level of risk and potential impact on the organization allows for proper prioritization of security investments. Often, cybersecurity receives fewer funds than other departments, and a reallocation of funds might be prudent. Consider what has a greater impact: being down for a week, unable to generate revenue, or not having a certain amount of money for a specific department?
The threat landscape
Business leaders should remain up to date on current threats and their relevance to the organization. Conducting regular threat assessments can help manage this information and inform the allocation of resources (whether they remain in-house or outsourced).
Technology infrastructure
In most incidents Blue Team Alpha has responded to, the attacked company’s technology infrastructure is outdated. Outdated tech is chock-full of weaknesses and vulnerabilities because they are often no longer supported or patched. Threat actors target this technology because it is easy to exploit.
People and planning
Cybersecurity training for employees at all levels of the business is critical. Employees are the weakest link in a security defense strategy—especially if they cannot identify potential threats. It only takes one person to click a malicious link or download a malicious file and compromise an entire system.
Companies need a clear, established incident response (IR) plan or policy that all relevant parties across the organization know. In most incidents Blue Team Alpha has responded to, the attacked company did not have an IR plan. Not having an IR plan is a critical missing piece because it increases time spent responding to an attack and restoring operations. The longer a company is down, the more money is lost.
Keep cybersecurity in-house or outsource to a 3rd party?
To answer the question above, there are several factors to consider. These include company size, revenue, security budget, industry, required cybersecurity expertise and cost options. Outsourcing cybersecurity has more flexibility because it’s easier to scale services up or down based on business needs. There is also the option to keep some in-house while outsourcing components not suited to your team’s skillset or budget. For instance, there could be enough in the budget to set up an in-house proactive defense, but not enough to have an incident response team. In that case, you would partner with a 3rd party IR firm.
Pre-boom versus post-boom investment prioritization
Pre-boom (pre-cyberattack) initiatives are proactive measures like staff training, controls implementation and access management. Focusing on preventative measures helps reduce the risk of attack. Alternatively, some believe focusing on post-boom (post-cyberattack) response efforts is smarter. This group operates with the mindset that “it’s not a matter of if, but when” you’ll be attacked. Ultimately, the return on investment (ROI) for this depends on the type of company. For example, healthcare organizations hold sensitive data, and if that data is stolen and leaked, regardless of how much post-boom infrastructure is in place, they have essentially already lost it.

Investing in a cybersecurity strategy
You have done the work and now have a cybersecurity budget: now what? Where do you start?
Implement basic cyber hygiene controls (compliance)
At Blue Team Alpha, we believe compliance is the starting point. Once a business is compliant, then it can implement other, stronger security measures.
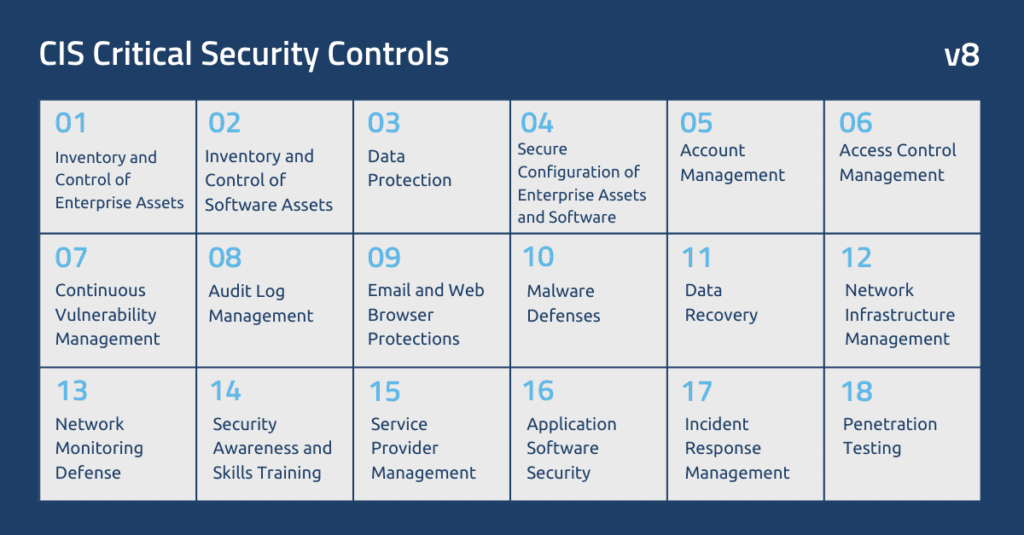
We recommend companies start with a cybersecurity assessment based on the Center for Internet Security (CIS) Critical Security Controls (CIS Controls) version 8 (v8) framework, beginning with Implementation Group 1 (IG1). CIS Controls are a prioritized set of safeguards to mitigate the most common cyberattacks against systems and networks.
An assessment provides an overview of cybersecurity strengths and weaknesses and indicates areas to focus on later. Businesses can prioritize the controls in IG1 based on their needs. For example, a healthcare organization might want to focus on data sensitivity controls to ensure it remains HIPAA compliant. Once an organization is at 90% or higher for IG1, the next step is Implementation Group 2 (IG2) and then Implementation Group 3 (IG3).
With a smaller cybersecurity budget, it is wise to start with IG1 and then move on to the other groups as the budget and organization mature. A broad range of basic controls is covered once the business is IG3 compliant. CIS Security Control Navigator is a tool to learn more about CIS Controls and Safeguards and see how they map to other security standards and frameworks.
Our top 5 controls within CIS Controls v8
Control 14: Security Awareness and Skills Training
As mentioned above, employees are the weakest link in a security posture. Most attacks result from the social engineering of employees. Proper—and consistent—awareness training is crucial in protecting the network.
Control 6: Access Control Management
Implementing strong access controls is critical to protecting sensitive data. Only those required should have access to sensitive data—not everyone in the organization. Including controls like privileged access management, data encryption and multifactor authentication (MFA) can prevent threat actors from accelerating privilege if they breach the network.
Control 7: Continuous Vulnerability Management
While a simple practice, regularly updating and patching systems should never be neglected or overlooked. Out-of-date systems leave vulnerabilities readily available for threat actors to exploit. Many incidents are a result of unpatched or out-of-date systems.
Control 9: Email and Web Browser Protections
Email security is vital because cybercriminals often use it as a platform to launch their attacks. By focusing on email security, organizations can reduce their risk of getting attacked (phishing is the most common type of cybercrime). This also reduces the risk of business email compromise (BEC), ransomware, spoofing and other scams from being successful.
Control 16: Application Software Security
For more mature organizations with higher budgets, it is worth investing in threat detection and response technologies like security information and event management (SIEM), endpoint detection and response (EDR) and security orchestration, automation and response (SOAR).
Using the FBI IC3 report to determine cybersecurity budget spend
Once compliance is achieved, the next steps should be informed by what is happening cybersecurity-wise in the world. We recommend downloading the FBI Internet Crime Complaint Center (IC3) report. The IC3 is a public resource to gather reports of cyberattacks and incidents, allowing the FBI to collect data, identify trends and respond to threats. This information provides a comprehensive analysis of reported cybercrimes across all states and industries, which can help determine the areas to focus cybersecurity budget spending.
Analyze trends
First, analyze cybersecurity trends to determine which threats likely will target your industry. These threats are what your security strategy should be working to prevent. For example, in 2022, healthcare was the top industry victimized by ransomware—so, for that industry, ransomware should be a key focus. Once determined, you should look at the data surrounding how much specific types of attack cost in your state. For example, the costs associated with being an attack victim as a healthcare provider in California are much higher than those of an IT service provider in Virginia.
Types of crime
Focusing your budget on the top ten crime types is an effective way to get the most value out of your security investments. Phishing is the most common attack type, and its prevention should be a priority for every company.
Evaluating risk
It is valuable to assess which threats cost the most or have the highest financial impact. Risk is calculated by looking at the most common threats in conjunction with the ones with the highest impact. The IC3 contains both facts. In 2022 the top four threats in terms of cost were investment scams, business email compromise (BEC), ransomware and call center fraud.
In addition, it is good practice to analyze and estimate the cost to your business if you shut down for a week compared to your security budget. For example, imagine your business will be down for one week a year because of a cyberattack and estimate it will cost $1 million (expected annual loss of $1M/year). This is the high point of your security budget, which you do not want to spend more than. Instead, you should aim to spend a percentage of that amount. 10% would be a budget of $100K/year to prevent a loss of $1M/year.
Conclusion
Cybersecurity is complicated, especially with the sheer volume of solutions and vendors available. This is why it is crucial to narrow down security strategies to focus on what is most relevant to your business—the threats posing the highest risk. Being strategic gets the most value out of a budget, even the small ones.
Blue Team Alpha is a one-stop cybersecurity shop—no matter what your needs are, we can fulfill them. Talk to an expert today to see how we can help.
We can complete a cybersecurity risk assessment based on the Center for Internet Security (CIS) Critical Security Controls (CIS Controls) version 8 (v8) framework or any of the following standards:
- HIPAA
- GDPR
- PCI
- FFIEC
- NYDFS
- HITRUST CSF
- NIST CSF
- NIST SP 800-171
- NIST 800-53
- ISO 27000-1
- SOC2
- SANS 20 CSC




