By now you’ve probably heard about the Microsoft Exchange hack, or the Hafnium attack—a cybersecurity cautionary tale circulating the news. But for many businesses around the globe, the attack is more than a story: it’s at their back door.
Over the past few weeks, an increasing number of breaches in Exchange Servers have forced Microsoft to act quickly. These multiple vulnerabilities have left companies utilizing older versions of Exchange wide-open to ransomware, malware, and other threats to sensitive data and business operations. While investigations are ongoing, Microsoft is strongly encouraging the following next steps:
1. Deploy updates to affected Exchange Servers.
2. Investigate for exploitation or indicators of persistence.
3. Remediate any identified exploitation or persistence and investigate your environment for indicators of lateral movement or further compromise.
In this post we’ll be addressing components of the attack chain, as well as questions like, “what is Microsoft Exchange, anyway?” and “what impact do these cyberattacks have on my business?”
What is Microsoft Exchange?
Essentially Microsoft Exchange is a piece of software that runs on a server and manages all of your emails. Whether incoming, outgoing, saved, in draft-mode, or scheduled on your calendar—everything is done through Microsoft Exchange and stored on a dedicated server.
Rather than burdening individual computers with loads of email storage, Microsoft Exchange provides several benefits: it centralizes emails so that they can be backed up, it eliminates threats before they reach your network, and it shares information (such as calendars) with different members of your organization.
Microsoft exchange servers are separate from cloud-based Office 365 servers, and usually exist on company premises.
What happened in the attack?
On March 2, Microsoft Threat Intelligence Center released information about multiple 0-day exploits that had been detected as early as January. These exploits, or unknown computer software vulnerabilities, were being used to attack versions of Microsoft Exchange. Microsoft also released several critical security patches to tackle these severe vulnerabilities in the Exchange Server software. At the time, the company said that the bugs were being actively exploited in limited, targeted attacks.
Eventually however, it came to light that over 30,000 organizations, according to Krebs on Security, “including a significant number of small businesses, towns, cities and local governments”, had been hacked.
In each incident, intruders left (and continue to leave behind) “web shells,” or easy-to-use, password-protected hacking tools that can be accessed over the Internet from any browser. Web shells provide attackers with a basic interface to access the victim’s computer servers. Microsoft even reported an uptick in worldwide web shell attacks back in February.
Very quickly, attackers were able to run automated scripts, scanning the internet for any Exchange Servers not yet protected by the patch updates that Microsoft had released. But security patches can only go so far: while these updates did “close the back door”, so to speak, they are not designed to eradicate threats presently in the network. In fact, leaving web shells behind was simply phase one of the attack.
“These vulnerabilities are being exploited as part of an attack chain. The initial attack requires the ability to make an untrusted connection to the Exchange server, but other portions of the attack can be triggered if the attacker already has access or gets access through other means. This means that mitigations such as restricting untrusted connections or setting up a VPN will only protect against the initial portion of the attack to change the attack surface or partially mitigate, and that patching is the only way to mitigate completely.”
In other words, once attackers have stayed dormant for a while in your network, they are soon able to conduct reconnaissance and gain credentials. Ransomware, malware, crypto-mining and other nefarious cyberattacks are only symptoms of the initial Microsoft Exchange breach. And unfortunately, the number of estimated victims continues to grow.
The primary goal of these cyberattackers is to steal information from an organization’s network. In some cases, this information is held for ransom, but in others, important payment or identity credentials are stolen entirely.
Who is behind these attacks?
Microsoft has traced these zero-day exploits back to a state-sponsored threat group known as Hafnium. While the group originates in China, they are able to conceal their exact location via virtual private servers located in the United States.
Historically, Hafnium primarily targets entities in the United States for the purpose of exfiltrating information from a number of industry sectors, including infectious disease researchers, law firms, higher education institutions, defense contractors, and policy think tanks.
That said, many other threat actors and groups are jumping on the bandwagon. Once news of security patch updates broke, Cyberforensics have shown that ransomware deployment and data theft are continuing (exponentially) in unpatched systems, and these attacks are conducted by malicious actors beyond Hafnium.
The Biden Administration is also forming a task force to explore these attacks further as well as determine any links between Microsoft Exchange and China.
What are the vulnerabilities?
An exchange server attack is fairly complex, but the Microsoft Security Blog has outlined its anatomy below:
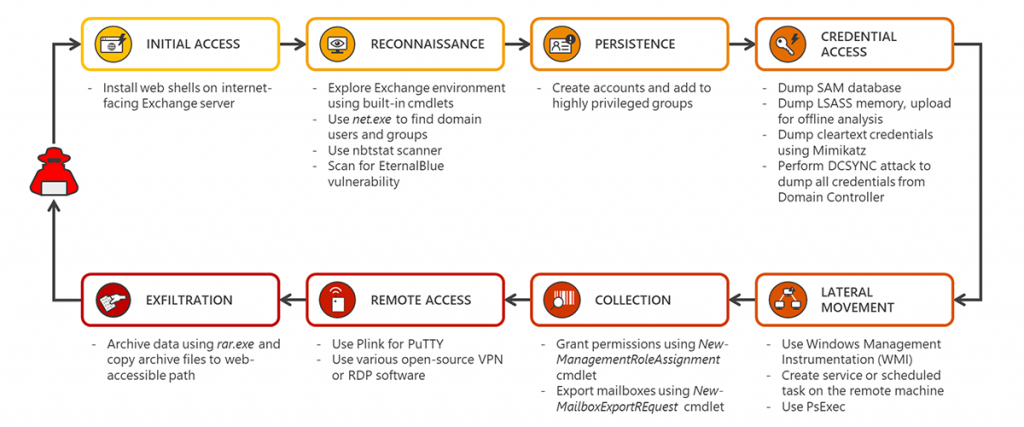
Microsoft also provided the following details to help customers understand the attack techniques used, and enable more effective defense against future attacks against unpatched systems.
- CVE-2021-26855 is a server-side request forgery (SSRF) vulnerability in Exchange which allowed the attacker to send arbitrary HTTP requests and authenticate as the Exchange server.
- CVE-2021-26857 is an insecure deserialization vulnerability in the Unified Messaging service. Insecure deserialization is where untrusted user-controllable data is deserialized by a program. Exploiting this vulnerability gave HAFNIUM the ability to run code as SYSTEM on the Exchange server. This requires administrator permission or another vulnerability to exploit.
- CVE-2021-26858 is a post-authentication arbitrary file write vulnerability in Exchange. If HAFNIUM could authenticate with the Exchange server then they could use this vulnerability to write a file to any path on the server. They could authenticate by exploiting the CVE-2021-26855 SSRF vulnerability or by compromising a legitimate admin’s credentials.
- CVE-2021-27065 is a post-authentication arbitrary file write vulnerability in Exchange. If HAFNIUM could authenticate with the Exchange server then they could use this vulnerability to write a file to any path on the server. They could authenticate by exploiting the CVE-2021-26855 SSRF vulnerability or by compromising a legitimate admin’s credentials.
Why is this attack important?
From an architectural standpoint, this was one of the most sophisticated attacks that we’ve ever encountered. Its scope was so broad that every industry has been affected without discrimination. In general, it’s easy to see a cyberattacker’s motivation in targeted attacks like phishing and ransomware. But if discovering a vulnerability is as simple as running a script, this puts an incident response plan in close, immediate perspective.
The US federal government implemented a set of CMMC compliance guidelines for precisely this purpose: to vet vendors and ensure that any company touching sensitive government data is secure in and of itself. It’s entirely possible that we may see similar compliance and regulation structures emerge after such an expansive attack, and across all industries.
“As of March 12, Microsoft and RiskIQ say at least 82,000 servers remain unpatched.” Additionally, “On March 15, Check Point Research said attack attempts have increased 10 times based on data collected between March 11 and March 15. The US, Germany, and the UK are now the most targeted countries. Government and military targets account for 23% of all exploit attempts, followed by manufacturing, financial services, and software vendors.”
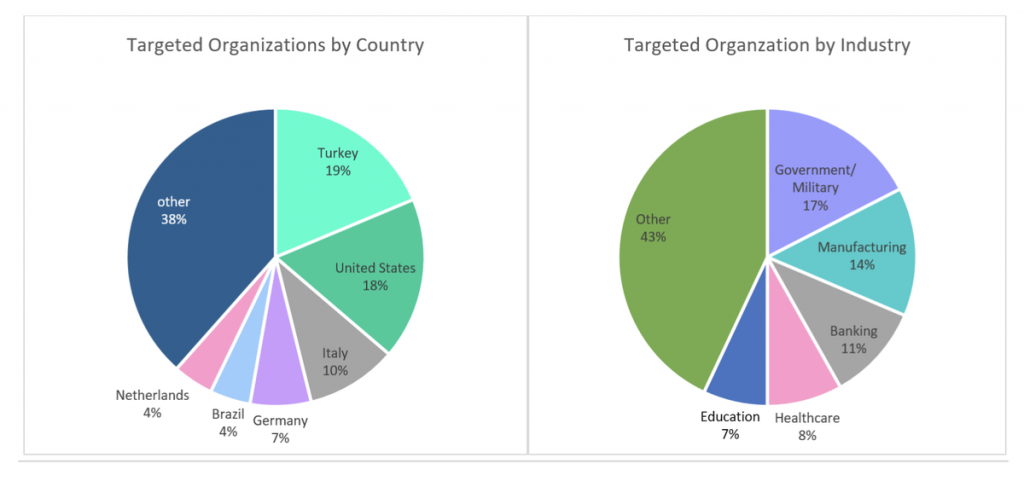
It’s worth considering, too, that much of the attack chain was automated. If companies were slow to patch, then attackers were able to take full advantage of scans and scripts to drop back doors and web shells into the environment. This has dramatic implications for the cybersecurity landscape in that as hackers develop bigger and bigger targets, companies will have to adapt proportionately.
Have I been compromised?
As always, it is best to be proactive rather than reactive if you believe you are one of the organizations that was impacted. The cost of a breach once a vulnerability has been exploited by an attacker is significantly more expensive to an organization in impacted systems, incident response costs, and most importantly, business continuity interruptions.
Microsoft is encouraging its customers to conduct investigations and implement proactive detections to identify possible prior campaigns and prevent future campaigns that may target their systems.
Remember: patching is not enough. While updates will close back doors, you may be shutting criminals inside the network with you. We have encountered dozens of incidents over the past week where dormant executables and powershells entered the environment before the patch updates. This means that your network is still vulnerable.
Without investigation and the proper tooling, threats may still be active in your network. Don’t leave vulnerabilities to chance and call your cybersecurity experts today: Blue Team Alpha will be able to identify issues in your network so that you can remediate any vulnerabilities before a bad actor exploits them. Reach out today so that we can answer one simple, but very important, question: is your organization compromised?




