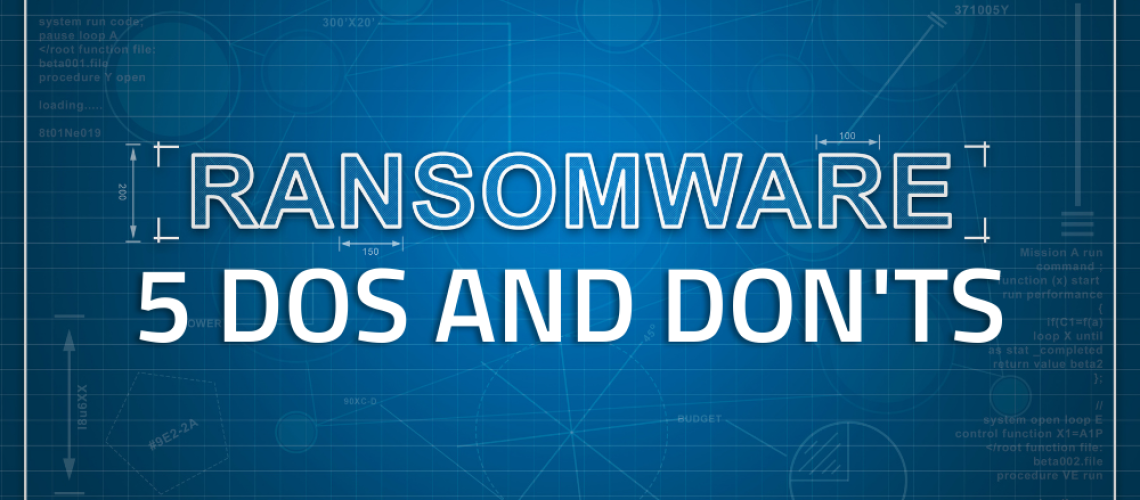
Walking in to a ransomware splash screen on your organizations’ computers can be terrifying; and trust us, ransomware attacks are designed to terrify. Often times untraceable bitcoin payments are involved (and sometimes even extortion demands) in order to gain access to your computer, sensitive files, or network.
Ransomware attacks are currently considered by many reports as the top cybersecurity threats, and for good reason. Not only is data theft a profitable industry, costing companies on average $761,106 per payout, but attackers have taken things a step further by publicly disclosing sensitive data on leak sites.
If you discover ransomware in your system, the most important thing to do first is not to panic. Taking the right steps as soon as you think an attack is underway can have a positive impact on the cost to your organization (cost and reputation).
Once you’ve been hit with ransomware, mitigation is key. We’ll review the following Dos and Don’ts below:
- Do isolate network traffic to mitigate the risk of continued adversary activity
- Do not turn off servers until you are certain they have not been affected by ransomware
- Do verify the state of business-critical system backups and make an offline copy of these backups
- Do contact legal counsel and inform them of the situation
- Do not try to “clean up” the ransomware without professional assistance
Learn More About Our…
$761,106 is the average cost of a ransomware attack in 2020.
(Sophos 2020 Report)
What is Ransomware and How Does it Work?
Ransomware is a form of malware (malicious software) that threatens to publish a victim’s data, or prevents access to their systems or personal files unless a ransom is paid. Files may be encrypted until a sum of money in cryptocurrency is paid in order to restore access.
Generally malware that enables an attacker to deploy ransomware arrives in the form an unsuspecting file or link in an email. For example, you could receive an email from what looks like your bank or workplace, asking you to “log in” to your “account”. The link would then redirect to a malicious, downloadable and executable file, thereby giving attackers a solid foothold into your system.
Once inside, hackers are able to move laterally, run scripting, and launch an attack. Check out our other blog article about the full anatomy of a cyberattack and how it can all start with a simple email.
23% of all cyberattacks in 2020 were ransomware attacks.
(IBM Threat Intelligence Index)
(IBM Threat Intelligence Index)
Signs of a Ransomware Attack
Typically when investigating an instance of ransomware, we look out for a variety of “indicators of compromise”, or things that look out of the ordinary in your network. Here are a few things to look out for if you’re not sure if ransomware is in your system, or if you’ve noticed something suspicious.
- Suspicious/unexpected money transfer
- Suspicious/unexpected vendor account change request
- Multiple failed login attempts (brute force)
- Abnormal remote login sessions
- Unauthorized email forwarding rules
- Logins from an unfamiliar domain
- Unopenable files
- Abnormal information system behavior
- Increased quantity and quality of phishing attempts
- Duplicate invoice complaints from multiple customers
If any of the above seem out of place, you’ll want to follow the below steps carefully in order to prevent further and future damage.
If You Suspect an Active Attack, Call or Contact Us 24/7/365
What to Do (and What Not to Do) if You are the Victim of a Ransomware Attack
You may be tempted to remove ransomware yourself once it’s discovered, but doing so could leave you susceptible to future attacks. Even if you find yourself wanting to pay the ransom right away, your data and reputation are still on the line. Follow these 5 tips below to achieve a quick resolution that doesn’t place your company and data at greater risk.
Step 1: DO isolate network traffic to mitigate the risk of continued adversary activity.
Once you determine there is an active ransomware attack, you need to stop the spread and prevent the attacker from maintaining their foothold on network connectivity. You can accomplish this by building “islands”. This way you slow and prevent traffic entirely within your network. We recommend blocking connections at the following locations:
- External firewall (to prevent any and all internet traffic and to keep the attackers out)
- Business-critical servers
- Any asset with indications of ransomware
- On-premise backup solutions
Step 2: DO NOT turn off servers until you are certain they have not been affected by ransomware.
The applications attackers use are often stored in the computer’s live memory. This is valuable forensic information that can be used to determine the most effective countermeasures against an attack. Restarting or rebooting assets clears the live memory, wiping out this valuable data. Servers should stay on, but must be isolated (see Step 1).
Step 3: DO verify the state of business-critical system backups and make an offline copy of these backups.
Attackers have invested time, and they want to get paid. They will often target backup solutions and, if found, delete them, to prevent the victim from rebuilding critical assets. An offline copy of the backups reduces the likelihood that all quality backups will be destroyed by ongoing ransomware efforts.
Step 4: DO contact legal counsel and inform them of the situation.
Every state has laws around breach disclosure that stipulate what you need to do if your organization has been the victim of an attack. It’s important to consult legal counsel with experience in cyber law to help you determine whether or not public disclosure of the event is required by law.
Step 5: DO NOT try to “clean up” the ransomware without professional assistance.
While it may be tempting to try and clean up a ransomware attack on your own, this can increase your chances of falling victim to a future attack. Once an adversary is inside your network, they can turn 1 back door into 5. Attackers also share information about successful attacks with fellow hackers. Proper hunting and remediation is key to future protection.
Download Our Checklist
The Real Cost of a Cyberattack
When most people think about ransomware, the cost of the ransom itself is what comes to mind. But much more than bitcoin is at stake when it comes to payment: there’s also downtime, people time, network cost, lost opportunity, and lost revenue to consider. When constructing an incident response plan, we recommend that organizations calculate how much a ransomware attack could cost their business.
To put it in context, an average North American business suffers about 14 hours of IT downtime per year, to the enormous detriment of SMBs and SMEs. Costs incurred can range from labor to record recovery to incident response. The figures below demonstrate the average revenue cost of downtime per year.
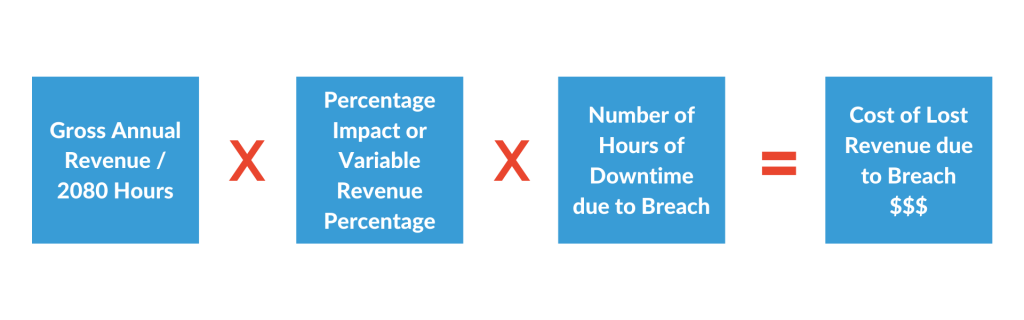
Simply take your gross annual revenue, divided by 2080 hours, and multiply that by the percentage impact or variable revenue percentage, and multiply that again by the number of hours of downtime due to a breach, and you’ll end up with the total cost of lost revenue due to a breach.
Ransomware is the most common cybersecurity threat today. The damage to your business crosses many areas, ranging from lost revenue and wages to lost data, legal costs, and penalty fees. Then, of course, there is the reputational damage that can have lingering effects on your business for years to come.
Why You Need to Act Quickly in the Event of a Ransomware Attack:
We have seen firsthand the costly impact of ransomware attacks and lengthy dwell times, with companies unaware they were even under attack in the first place. One company suffered a loss of $150,000 with the attack having a dwell time of six months. Another company also saw a dwell time of six months and lost $750,000 in less than 30 days. Yet another victim was losing money at a rate of $10,000 per hour, with an attacker in their system for more than three months.
How Blue Team Alpha Can Help
Long dwell times point to the fact that many organizations just simply aren’t aware they are under attack until it is too late. Learn how Blue Team Alpha can assist with a Compromise Assessment and a Ransomware Emergency Response to name a few. You can also find out more by downloading our Ransomware Response Checklist or by contacting us today!