What Happened?
On July 2nd, 2021, Kaseya, an IT solutions developer for MSPs and enterprise clients, announced that it had become victim to a cyberattack. Kaseya immediately encouraged its customers to shut down VSA (Virtual System/Server Administrator) servers in order to prevent further access to attackers. VSA software is used by Kaseya customers to remotely monitor and manage software and network infrastructure, and is supplied either as a hosted cloud service by Kaseya, or via on-premises VSA servers.
The cyberattack involved ransomware which was pushed via an automated, fake, and malicious software update. The update appeared to users as “Kaseya VSA Agent Hot-fix”, but the fake patch was actually REvil ransomware. REvil is a suspected Russia-based hacking group that has been linked to several other major breaches. Once deployed, zero-day vulnerabilities were exploited by the attackers to trigger a bypass authentication and for code execution, allowing them to infect endpoints with ransomware.
While Kaseya did pull SaaS data centers offline, resulting in only 40 affected customers or fewer worldwide, the impact on SMBs and MSPs further down the supply chain remains to be seen.
Attack Details
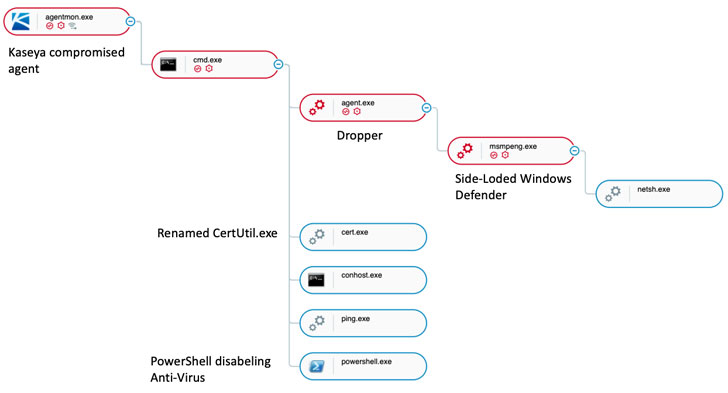
According to a statement from the FBI this is a “supply chain ransomware attack leveraging a vulnerability in Kaseya VSA software against multiple MSPs and their customers.” In recent announcements, Kaseya disclosed that it is now dealing with ransomware that may be affecting at least eight MSPs and hundreds of organizations. The above image illustrates the attack flow of these VSA vulnerabilities.
The attackers were able to exploit zero-day vulnerabilities in the VSA product to bypass authentication and run arbitrary command execution. This allowed the attackers to leverage the standard VSA product functionality to deploy ransomware to endpoints. There is no evidence that Kaseya’s VSA codebase has been maliciously modified.
Kaseya HelpDesk
On July 2nd, REvil actors said that they would be willing to provide a universal decryptor for victims of the attack, but under the condition that they be paid $70,000,000 worth of BitCoin.

CISA and FBI recommend affected MSPs:
• Download the Kaseya VSA Detection Tool. This tool analyzes a system (either VSA server or managed endpoint) and determines whether any indicators of compromise (IOCs) are present.
• Enable and enforce multi-factor authentication (MFA) on every single account that is under the control of the organization, and—to the maximum extent possible—enable and enforce MFA for customer-facing services.
• Implement allowlisting to limit communication with remote monitoring and management (RMM) capabilities to known IP address pairs, and/or
• Place administrative interfaces of RMM behind a virtual private network (VPN) or a firewall on a dedicated administrative network.
CISA and FBI recommend affected MSP customers:
• Ensure backups are up to date and stored in an easily retrievable location that is air-gapped from the organizational network;
• Revert to a manual patch management process that follows vendor remediation guidance, including the installation of new patches as soon as they become available;
• Implement: Multi-factor authentication; and Principle of least privilege on key network resources admin accounts.
Indicators of Compromise
Be sure to check out our other blog post about what to do and what not to do if you’re the victim of a ransomware attack. But in the meantime, here are a few things to look for within your network:
• Suspicious/unexpected money transfer
• Suspicious/unexpected vendor account change request
• Multiple failed login attempts (brute force)
• Abnormal remote login sessions
• Unauthorized email forwarding rules
• Logins from an unfamiliar domain
• Un-openable files
• Abnormal information system behavior
• Increased quantity and quality of phishing attempts
• Duplicate Invoice complaints from multiple customers
If You Were Impacted
Ransomware and related cyberattacks are on the rise. As always, it is best to be proactive rather than reactive if you believe you are one of the organizations that could be impacted. The cost of a breach once a vulnerability has been exploited by an attacker is significantly more expensive to an organization in impacted systems, incident response costs, and most importantly, business continuity interruptions.
Have I Been Compromised?
CISA is encouraging companies that may have been compromised to conduct investigations and implement proactive detections to identify possible prior campaigns and prevent future campaigns that may target their systems. Blue Team Alpha will be able to identify issues in your network so that you can remediate any vulnerabilities before a bad actor exploits them. Reach out today so that we can answer one simple, but very important, question: is your organization compromised?




